Cyber resilience helps businesses anticipate, withstand, and recover from cyberattacks, ensuring continuity even when breaches occur.
What is Cyber Resilience? Beyond Traditional Cybersecurity
In today’s relentless digital landscape, the question for businesses isn’t if you’ll face a cyberattack, but when. This harsh reality necessitates a shift in focus from mere prevention to something more robust: Cyber Resilience. It’s the ability of an organization to not just defend against cyber threats, but to anticipate, withstand, recover from, and adapt to them, ensuring business continuity even in the face of a breach or incident.
Think of it this way:
- Cybersecurity is your defensive line – the firewalls, antivirus, and policies designed to stop attacks from getting in. It’s crucial, but it assumes you can block everything.
- Cyber Resilience acknowledges that some attacks will get through. It’s your entire team’s ability to take the hit, stay on your feet, and keep moving forward. It’s about minimizing damage, restoring operations quickly, and learning from every encounter to become stronger.
A truly cyber resilient organization operates through a continuous cycle of four key phases:
- Anticipate: Proactively identify potential threats, vulnerabilities, and the likely impact of an attack. This involves threat intelligence, risk assessments, and understanding your critical assets.
- Withstand: Implement controls and safeguards to resist an attack. This includes robust security measures, redundancy, and incident response planning that minimizes disruption during an event.
- Recover: Rapidly restore systems, data, and operations after an incident. This relies on effective backup strategies, disaster recovery plans, and swift incident response execution.
- Adapt: Learn from every incident (whether internal or external) and continuously improve your security posture and resilience strategies. This ensures your defenses evolve faster than the threats.
Cyber resilience moves beyond simply “being secure” to ensuring your business can endure the inevitable and emerge stronger.
Why Cyber Resilience is Non-Negotiable for Modern Businesses
In an interconnected world, digital operations are the lifeblood of almost every business. This dependence means that any significant cyber disruption can cascade into devastating consequences. Cyber resilience isn’t just a buzzword; it’s a fundamental requirement for survival and growth in the face of escalating threats.
Here’s why building cyber resilience is non-negotiable for modern businesses:
- Ensuring Business Continuity: Your ability to continue operating during and after a cyberattack is paramount. Cyber resilience ensures that even if a system goes down, or data is compromised, your critical business functions can remain operational or be restored quickly, preventing costly downtime and lost revenue.
- Mitigating Severe Financial Impact: The cost of a cyberattack extends far beyond initial remediation. It includes lost revenue, regulatory fines, legal fees, reputation damage, and increased insurance premiums. According to the IBM Cost of a Data Breach Report 2024, the global average cost of a data breach is a staggering $4.88 million. A strong cyber resilience strategy significantly mitigates these financial blows.
- Protecting Your Reputation and Customer Trust: News of a cyberattack or data breach can severely tarnish your brand’s reputation. Customers lose trust in businesses that can’t protect their data, leading to customer churn and difficulty acquiring new clients. Cyber resilience demonstrates a commitment to safeguarding sensitive information, reinforcing trust.
- Meeting Regulatory Compliance Demands: A growing number of industry regulations and data privacy laws (e.g., GDPR, HIPAA, PCI DSS) impose strict requirements for data protection and incident response. Organizations with robust cyber resilience are better positioned to meet these compliance obligations, avoiding hefty fines and legal repercussions.
- Gaining a Competitive Advantage: In a marketplace where cyber threats are a constant concern, businesses with proven cyber resilience stand out. It signals reliability and trustworthiness to partners, investors, and customers, potentially attracting more business and securing partnerships.
- The “When, Not If” Mindset: As mentioned earlier, no organization is entirely immune to cyberattacks. Embracing a “when, not if” mindset means proactively preparing for incidents, rather than reactively scrambling once they occur. This proactive stance is the essence of resilience.
Cyber resilience shifts your organization from a reactive victim to a prepared survivor. It’s no longer an optional add-on; it’s a core strategic imperative for every forward-thinking business.
The Core Pillars of a Robust Cyber Resilience Strategy
Building true cyber resilience requires a structured, multi-faceted approach. It’s not about deploying a single tool, but rather integrating various components into a cohesive strategy. Think of these as the fundamental pillars that support your organization’s ability to bounce back from any cyber challenge.
A robust cyber resilience strategy is built upon these core pillars:
- 1. Governance & Risk Management:
- What it is: Establishing clear leadership, policies, and processes for cybersecurity. Identifying, assessing, and prioritizing cyber risks across your entire organization.
- Why it’s crucial: You can’t protect what you don’t understand. This pillar lays the foundation by defining who is responsible, what assets need protecting, and what threats are most relevant.
- 2. Protect:
- What it is: Implementing preventative technical and procedural controls to reduce vulnerabilities and defend against attacks. This includes firewalls, antivirus, intrusion detection, access controls, encryption, and secure configurations.
- Why it’s crucial: This is your first line of defense, aiming to stop threats before they can cause harm.
- 3. Detect:
- What it is: Establishing capabilities to identify and alert on cyber incidents as quickly as possible. This involves security monitoring, threat intelligence, security information and event management (SIEM), and endpoint detection and response (EDR) solutions.
- Why it’s crucial: The faster you detect an incident, the less damage it can cause. Early detection is key to limiting an attacker’s dwell time.
- 4. Respond:
- What it is: Having pre-defined plans and procedures to manage and contain a cyber incident once it’s detected. This includes incident response plans, communication strategies, and dedicated response teams.
- Why it’s crucial: A rapid, coordinated response minimizes the spread of an attack, limits data loss, and accelerates recovery.
- 5. Recover:
- What it is: Restoring compromised systems, data, and services to normal operation. This involves robust data backup and recovery strategies, disaster recovery plans, and business continuity plans.
- Why it’s crucial: This pillar ensures your business can resume operations quickly, minimizing downtime and its associated costs.
- 6. Adapt & Learn:
- What it is: Continuously evaluating your cyber resilience posture based on past incidents, emerging threats, and new technologies. Incorporating lessons learned into revised strategies and controls.
- Why it’s crucial: The threat landscape is constantly changing. This pillar ensures your resilience strategy evolves, making you stronger and more prepared for future challenges.
By meticulously building and maintaining each of these pillars, businesses can create a truly resilient ecosystem that can withstand the inevitable shocks of the cyber world.
Cyber Resilience vs. Cybersecurity: Understanding the Critical Difference
Often, the terms cyber resilience and cybersecurity are used interchangeably. While intimately related and interdependent, they represent distinct concepts with different primary goals.
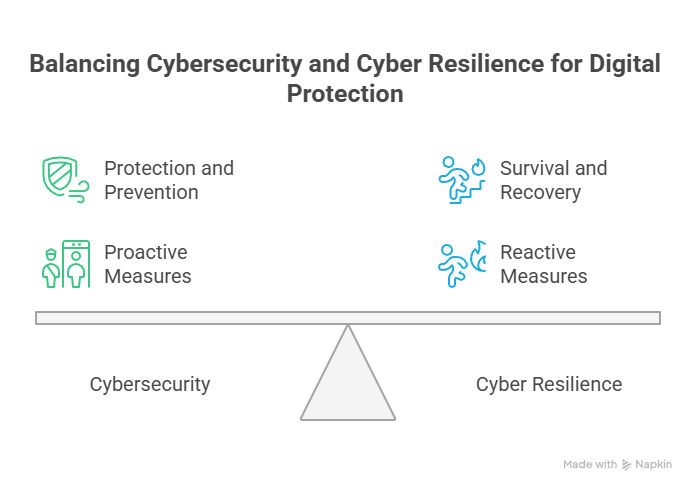
Understanding this critical difference is fundamental to building a truly effective and comprehensive defense strategy for your business.
The Complementary Nature:
Neither cyber resilience nor cybersecurity can stand alone effectively. They are two sides of the same coin, each strengthening the other:
- Strong Cybersecurity Enables Resilience: Robust preventative cybersecurity reduces the frequency and severity of incidents, giving your resilience capabilities less to contend with. If fewer attacks get through, your recovery processes are needed less often.
- Cyber Resilience Makes Cybersecurity More Effective: By assuming breaches will occur, resilience forces you to build robust detection, response, and recovery mechanisms. This means that when cybersecurity defenses inevitably fail, your organization isn’t crippled. It can rapidly contain and bounce back, minimizing the impact of the cyber “failure.”
In essence, cybersecurity aims to win every battle, while cyber resilience ensures you win the war. Modern businesses must invest in both, integrating them into a unified strategy to protect their assets and ensure long-term viability.
Building a Cyber Resilient Workforce: The Human Element
In the complex tapestry of cyber resilience, technology and robust processes are vital, but they’re incomplete without the most crucial thread: the human element. Your employees are not just users; they are your first line of defense and a critical component of your ability to withstand and recover from cyberattacks. A truly cyber resilient organization empowers its workforce to be vigilant, knowledgeable, and proactive.
Here’s how to build a cyber resilient workforce:
- Continuous Security Awareness Training: This goes beyond annual checkboxes. Training should be:
- Engaging and Relevant: Use real-world examples of phishing, social engineering (like vishing), and common scams your employees might encounter.
- Interactive: Incorporate quizzes, simulated attacks (e.g., mock phishing campaigns), and discussions to reinforce learning.
- Timely: Update training regularly to reflect new threats and attack vectors.
- The Verizon Data Breach Investigations Report 2024 indicates that 68% of data breaches involve a human element, underscoring the direct impact of employee behavior on your security posture.
- Fostering an Incident Reporting Culture: Create an environment where employees feel safe and empowered to report suspicious activity immediately, without fear of blame.
- Clear Reporting Channels: Make it easy to report. Provide a dedicated email, phone number, or internal tool for reporting suspicious emails, calls, or system anomalies.
- Positive Reinforcement: Acknowledge and thank employees for reporting, even if it turns out to be a false alarm. This encourages continued vigilance.
- Role-Specific Training: Not all employees face the same risks. Tailor training to specific roles (e.g., finance team for wire fraud, IT staff for incident response procedures).
- Practice with Tabletop Exercises: Conduct regular tabletop exercises where teams walk through hypothetical cyberattack scenarios. This helps employees understand their roles, identify communication gaps, and test response plans in a low-stress environment.
- Promoting a Culture of Skepticism and Verification: Encourage employees to question unexpected requests, verify identities through alternative channels (e.g., calling back a known number), and avoid clicking suspicious links.
- Cyber Hygiene Best Practices: Reinforce fundamental cyber hygiene, such as strong, unique passwords, the use of Multi-Factor Authentication (MFA), and understanding safe Browse habits.
Your employees are not just vulnerable targets; they are your eyes and ears. By investing in them through continuous education and fostering a supportive, security-conscious culture, you transform them into active participants in your cyber resilience strategy, significantly enhancing your ability to withstand threats.
Leveraging Technology for Enhanced Cyber Resilience
While human vigilance is indispensable, modern cyber resilience heavily relies on sophisticated technology. The right tools can automate defenses, accelerate detection, streamline recovery, and provide the insights needed to adapt faster than attackers. Technology amplifies your human and process capabilities, creating a more robust defense-in-depth strategy.
Here’s how businesses can leverage technology for enhanced cyber resilience:
- Robust Data Backup & Recovery Solutions:
- Immutable Backups: Implement backups that cannot be altered or deleted by ransomware, providing an uncorrupted copy for recovery.
- Off-site and Offline Storage: Store critical backups physically separated or air-gapped from your network to protect against widespread attacks.
- Automated Backup Verification: Regularly test your backup restoration process to ensure data integrity and speedy recovery times.
- Advanced Threat Detection with AI/ML:
- Endpoint Detection and Response (EDR) / Extended Detection and Response (XDR): These tools go beyond traditional antivirus to continuously monitor endpoints and networks for anomalous behavior, leveraging AI and machine learning to detect and respond to sophisticated threats that bypass initial defenses.
- Security Information and Event Management (SIEM): Aggregate security logs from across your entire infrastructure, using AI to identify patterns and alert on potential incidents far faster than manual analysis.
- Secure Architectures (e.g., Zero Trust):
- Zero Trust Network Access (ZTNA): Implement a “never trust, always verify” model for all access requests, regardless of location. This dramatically limits lateral movement by attackers even if initial access is gained.
- Network Segmentation: Divide your network into smaller, isolated segments. This confines breaches to a smaller area, preventing them from spreading across your entire organization.
- Security Automation and Orchestration (SOAR):
- Automated Playbooks: Use SOAR platforms to automate repetitive incident response tasks, such as isolating infected devices, blocking malicious IPs, or initiating data recovery. This speeds up response times and reduces human error.
- Threat Intelligence Integration: Automate the ingestion and analysis of threat intelligence feeds to proactively update defenses and identify new risks.
- Cloud Security Posture Management (CSPM) & Cloud Workload Protection Platforms (CWPP):
- For organizations heavily reliant on cloud services, these tools ensure cloud environments are securely configured, continuously monitor for misconfigurations, and protect cloud workloads against runtime threats.
- Vulnerability Management & Patching Automation: Regularly scan for vulnerabilities in your systems and automate the patching process wherever possible. Proactive patching significantly reduces the attack surface.
By strategically deploying and integrating these technologies, businesses can create a resilient digital environment that not only protects against current threats but also adapts to and recovers from the unknown challenges of tomorrow.
Developing Your Cyber Resilience Framework & Incident Response Plan
Knowing about cyber resilience is one thing; putting it into practice is another. The backbone of a truly resilient organization is a well-defined Cyber Resilience Framework and a meticulously crafted Incident Response Plan. These aren’t just documents; they are living blueprints that guide your organization through the chaos of a cyberattack.
Here are practical steps for developing these critical components:
- 1. Establish Your Cyber Resilience Framework:
- Adopt a Standard: Start by aligning with a recognized framework like NIST Cybersecurity Framework, ISO 27001, or CIS Controls. These provide a structured approach to identifying, protecting, detecting, responding to, and recovering from cyber incidents.
- Identify Critical Assets: Conduct a Business Impact Analysis (BIA) to pinpoint your most crucial systems, data, and business processes. Understand their dependencies and the financial/operational impact if they’re compromised or unavailable. This tells you what to protect most fiercely and recover first.
- Define Roles and Responsibilities: Clearly assign who is responsible for what during a cyber incident – from detection to communication to technical recovery. Avoid ambiguity that can lead to delays.
- 2. Develop a Comprehensive Incident Response Plan (IRP):
- Preparation: This phase is all about readiness.
- Incident Response Team (IRT): Form a dedicated team with diverse skills (IT, legal, PR, HR, management).
- Tools & Technologies: Ensure you have the necessary security tools (SIEM, EDR, forensic tools) and secure communication channels.
- Playbooks/Runbooks: Create detailed, step-by-step guides for responding to common incident types (e.g., ransomware, phishing, data breach).
- Detection & Analysis:
- Define clear thresholds and indicators of compromise (IOCs).
- Establish procedures for logging, analyzing, and triaging alerts.
- Containment:
- Outline immediate actions to limit the spread of an attack (e.g., network segmentation, isolating infected systems, blocking malicious IPs).
- Eradication:
- Detail steps to remove the root cause of the incident and all remnants of the attacker’s presence.
- Recovery:
- Specify procedures for restoring systems and data from secure backups.
- Prioritize recovery based on your BIA.
- Post-Incident Activity (Lessons Learned):
- Conduct a thorough post-mortem analysis to identify what went well, what went wrong, and what needs improvement in your framework and plan.
- Preparation: This phase is all about readiness.
- 3. Practice with Tabletop Exercises and Drills:
- Simulate Scenarios: Regularly conduct realistic tabletop exercises where key stakeholders walk through hypothetical cyberattack scenarios. This helps test your IRP, identify gaps, and improve team coordination.
- Live Drills: For critical systems, perform actual recovery drills (e.g., restoring data from backups) to ensure technical capabilities are sound.
- 4. Establish Communication Plans:
- Define who communicates with whom (internally and externally) during an incident. This includes employees, customers, partners, regulators, and the media.
- Prepare pre-approved communication templates.
A well-structured framework and a practiced incident response plan are the cornerstones of truly effective cyber resilience, enabling your business to navigate the storm and emerge stronger.
Measuring and Improving Cyber Resilience Over Time
Building cyber resilience isn’t a one-time project; it’s a continuous journey. To truly achieve enduring resilience, organizations must have mechanisms in place to measure their progress, identify areas for improvement, and adapt their strategies in response to an ever-evolving threat landscape. Without measurement, improvement is guesswork.
Here’s how to measure and continuously enhance your cyber resilience:
- Define Key Performance Indicators (KPIs): Establish measurable metrics to track your resilience over time. Examples include:
- Mean Time to Detect (MTTD): How long it takes to identify a cyber incident. Lower is better.
- Mean Time to Respond (MTTR): How long it takes to contain an incident after detection. Lower is better.
- Mean Time to Recover (MTTRc): How long it takes to restore affected systems and data to normal operations. Lower is better.
- Number of Successful Phishing/Vishing Attempts: Track how many employees fall for simulated attacks.
- Patching Cadence & Compliance: Percentage of systems patched within a defined timeframe.
- Backup Success Rate & Restoration Time: Percentage of successful backups and time taken to restore critical data.
- Regular Audits and Assessments:
- Third-Party Audits: Engage independent experts to conduct regular security audits, penetration tests, and vulnerability assessments. These provide an objective view of your strengths and weaknesses.
- Compliance Audits: Ensure your resilience efforts align with regulatory requirements and conduct internal checks.
- Incident Post-Mortems and Lessons Learned:
- Formal Reviews: After every significant cyber incident (or even a close call), conduct a thorough post-mortem analysis.
- Identify Root Causes: Determine why the incident occurred and why existing controls failed (or succeeded).
- Document Lessons Learned: Capture insights into what could be improved in your processes, technology, and people training.
- Actionable Improvements: Translate lessons learned into concrete actions and integrate them back into your cyber resilience framework, policies, and training programs.
- Maturity Models: Utilize recognized cyber resilience maturity models (e.g., based on NIST CSF or industry-specific frameworks) to assess your current level of resilience and define a roadmap for advancing to higher maturity levels.
- Threat Intelligence Integration: Continuously ingest and analyze external threat intelligence to understand emerging attack techniques and adapt your defenses proactively.
- Feedback Loops: Establish strong feedback loops between your IT/security teams, business units, and leadership. Encourage open communication about risks, incidents, and improvement initiatives.
By embracing a culture of continuous improvement and leveraging data-driven insights, businesses can ensure their cyber resilience strategy remains effective, adaptive, and capable of protecting against the ever-evolving landscape of cyber threats.
GiaSpace: Your Partner in Achieving Enduring Cyber Resilience
In an age where cyberattacks are an inevitable reality, your business needs more than just defenses – it needs the ability to absorb the hit, recover swiftly, and emerge stronger. At GiaSpace, we understand that true Cyber Resilience is the cornerstone of modern business continuity. We don’t just provide security tools; we partner with you to build a comprehensive, adaptive framework that ensures your operations endure, no matter the cyber storm.
Navigating the complexities of cyber risk management, incident response, and continuous adaptation can be overwhelming. GiaSpace brings the expertise, strategic insights, and practical solutions to make your organization not just secure, but truly resilient.
Here’s how GiaSpace guides your organization toward enduring cyber resilience:
- Holistic Risk Assessment & Strategy Development: We begin by conducting thorough assessments to understand your critical assets, unique threat landscape, and current security posture. We then work with you to develop a tailored cyber resilience strategy that aligns with your business objectives and regulatory requirements.
- Proactive Protection & Detection: GiaSpace deploys and manages industry-leading cybersecurity technologies – from advanced endpoint protection and network security to AI-driven threat intelligence and SIEM solutions. We ensure you have robust defenses and the capability to detect even the most sophisticated attacks rapidly.
- Expert Incident Response Planning & Support: We help you develop, document, and most importantly, practice your Incident Response Plan. Our experts guide you through tabletop exercises and provide immediate, expert support during an actual incident, minimizing downtime and damage.
- Robust Data Recovery & Business Continuity: We design and implement resilient backup and disaster recovery solutions, including immutable storage, to ensure your critical data is always recoverable and your business operations can resume swiftly after any disruption.
- Building a Resilient Workforce: Recognizing the critical human element, GiaSpace offers engaging and continuous security awareness training programs. We empower your employees to be vigilant defenders, fostering a culture of security and proactive reporting.
- Continuous Improvement & Adaptation: We believe resilience is an ongoing journey. GiaSpace provides continuous monitoring, performance measurement, and regular audits to identify areas for improvement. We help you learn from every incident and adapt your defenses to stay ahead of evolving threats.
- Alignment with Industry Frameworks (NIST, ISO): Our strategies are built upon established industry best practices and frameworks, ensuring your resilience efforts are structured, comprehensive, and auditable.
- Managed Security Services: Focus on your core business while GiaSpace manages your complex security environment. Our 24/7 managed security services ensure constant vigilance, rapid response, and peace of mind.
Don’t wait for a breach to build your resilience. Partner with GiaSpace to transform your cybersecurity posture from reactive defense to enduring operational strength. Contact GiaSpace today for a comprehensive cyber resilience assessment and secure your business’s future against any digital challenge.
Published: Jun 18, 2025







