Every organization needs a bulwark against cyber threats in today’s digital landscape. This isn’t just a suggestion—it’s imperative. Without a strategic incident response plan, you’re setting your organization up for potential disaster. Let’s delve deeper into creating a robust plan that protects and prepares.
Understanding the Importance of an Incident Response Plan
While cybersecurity insurance policies may mandate an incident response plan, the reality is that every organization, regardless of size or industry, should have one. This isn’t about compliance—it’s about being proactive. A well-defined plan ensures that your team won’t be scrambling in panic when a cybersecurity incident occurs (and it’s often a matter of when, not if). Instead, they’ll have a step-by-step guide to counteract the threat.

Why is a Robust Incident Response Plan Absolutely Critical for Florida Businesses?
In today’s interconnected world, cyberattacks are not a matter of “if,” but “when.” For businesses across Florida – from the bustling tourism hubs of Orlando and Miami to the growing tech sectors of Gainesville and Jacksonville – a robust incident response plan (IRP) isn’t just a best practice; it’s a critical lifeline. Without a pre-defined strategy, a security incident can quickly spiral into a full-blown crisis, leading to massive financial losses, irreparable reputational damage, legal liabilities, and prolonged operational downtime. A well-crafted IRP empowers your business to detect, contain, and recover from cyber threats swiftly, minimizing their impact and safeguarding your assets, customer data, and ultimately, your future. It’s the difference between a minor setback and a catastrophic failure.
| Key Statistic | Value / Impact | Source / Context |
|---|---|---|
| Average Cost of Data Breach (2024) | $4.88 Million (Global Avg.) | IBM’s 2024 Cost of a Data Breach Report. For organizations with less than 500 employees, the average cost was approximately $3.31M. |
| Time to Detect & Contain Breach | 258 Days (Avg. global lifecycle) | IBM Security X-Force Threat Intelligence Index 2024. Breaches exceeding 200 days incurred significantly higher costs. |
| Cost Savings with IRP Testing | Up to $1.49 Million (Avg. cost reduction per breach) | Organizations that regularly test their Incident Response plans save significantly on breach costs (data referenced from IBM’s 2024 Cost of a Data Breach Report indicates those with IR teams and robust security testing save $248K on average, with other data indicating savings up to $2.66M for extensive use of AI and automation for prevention). |
What are the Essential Phases of a Modern Incident Response Plan (NIST Framework Explained)?
A structured approach is vital for effective incident response. The National Institute of Standards and Technology (NIST) provides a widely adopted framework, breaking down the process into six essential phases. Understanding and implementing each phase is crucial for comprehensive incident management:
- Preparation: This foundational phase involves establishing policies, procedures, and training for your incident response team before an incident occurs. It includes identifying critical assets, conducting risk assessments, and setting up necessary tools and communication channels.
- Identification: The moment an anomaly or potential security incident is detected. This phase focuses on determining if an incident has occurred, its scope, and its nature through monitoring, alerts, and analysis.
- Containment: Once identified, the immediate priority is to stop the spread of the incident and prevent further damage. This might involve isolating affected systems, disconnecting networks, or patching vulnerabilities to prevent recurrence.
- Eradication: After containment, the goal is to eliminate the root cause of the incident. This means removing malware, patching systems, or addressing vulnerabilities that led to the compromise.
- Recovery: Bringing affected systems back online and restoring normal operations. This involves validating system integrity, restoring data from backups, and continuously monitoring to ensure the threat is fully neutralized.
- Post-Incident Activity (Lessons Learned): A critical but often overlooked phase. This involves documenting the incident, conducting a thorough review to identify what went well and what could be improved, updating policies, and enhancing future preparedness. This iterative learning process strengthens your defenses over time.
What Key Roles and Responsibilities Form an Effective Incident Response Team?
A robust Incident Response Plan is only as strong as the team executing it. An effective Incident Response Team (IRT) is multidisciplinary, with clearly defined roles and responsibilities to ensure a coordinated and efficient response. Key roles typically include:
- Incident Response Manager/Coordinator: The central point of contact, responsible for overseeing the entire response, coordinating activities, and communicating with stakeholders.
- Technical Lead/Analysts: The hands-on experts who investigate the incident, analyze forensic data, identify the root cause, and implement containment and eradication measures.
- Legal Counsel: Advises on legal obligations, compliance requirements, and potential liabilities arising from the incident, including data breach notification laws (crucial for Florida businesses).
- Public Relations/Communications: Manages external communications (media, customers, public) to control narrative, protect reputation, and ensure transparency where necessary.
- Human Resources: Handles internal employee communications, potential HR-related issues stemming from the incident, and support for affected staff.
- Senior Leadership/Executive Sponsor: Provides strategic oversight, approves resources, and makes high-level decisions.
- Law Enforcement Liaison (if applicable): Coordinates with law enforcement agencies if criminal activity is suspected or required by law.
- External Experts (e.g., GiaSpace): For specialized incidents or to augment internal capabilities, external cybersecurity firms provide crucial expertise in forensics, remediation, and strategic advice.
How to Develop a Step-by-Step Incident Response Strategy for Your Business?
Developing an incident response strategy requires a systematic approach tailored to your specific business needs. This isn’t a “one-size-fits-all” template, but rather a dynamic document that evolves with your organization and the threat landscape.
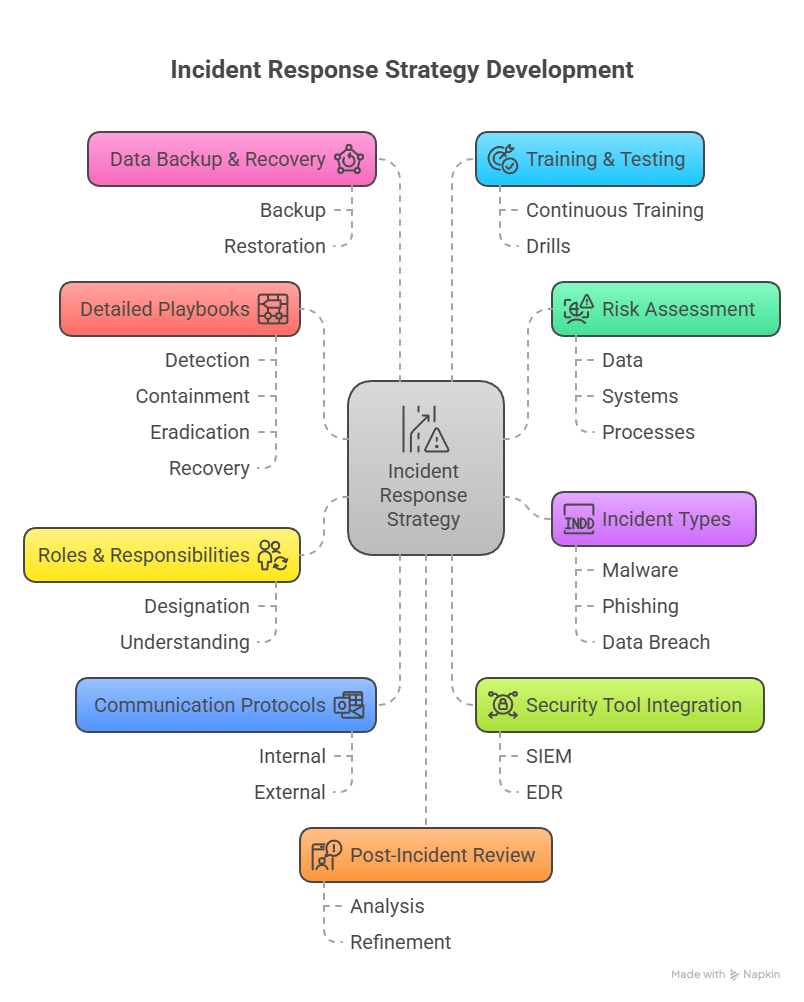
Here’s a step-by-step guide:
- Assess Your Risks & Critical Assets: Identify what data, systems, and processes are most vital to your business. Understand potential threats and vulnerabilities to prioritize your response efforts.
- Define Incident Types: Categorize common incidents (e.g., malware, phishing, data breach, denial-of-service) to standardize response procedures.
- Establish Clear Roles & Responsibilities: As discussed, designate who does what, when, and how. Ensure everyone understands their part.
- Outline Communication Protocols: Define internal and external communication plans. Who needs to know? When? How? Include templates for notifications.
- Develop Detailed Playbooks: For each incident type, create step-by-step “playbooks” or workflows outlining detection, containment, eradication, and recovery procedures.
- Integrate with Existing Security Tools: Ensure your IRP leverages your existing security information and event management (SIEM), endpoint detection and response (EDR), and other cybersecurity tools.
- Plan for Data Backup & Recovery: Critical for business continuity, your IRP must include clear strategies for data backup, restoration, and system recovery.
- Regular Training & Testing: An IRP is a living document. Continuously train your team and conduct drills to ensure readiness.
- Post-Incident Review: Build a process for analyzing every incident to learn from it and refine your plan.
What are the Best Practices for Testing and Continuously Improving Your IRP?
An Incident Response Plan is not a static document; its effectiveness hinges on regular testing and continuous improvement. Neglecting this crucial step can render your plan useless when a real incident strikes. Follow these best practices:
- Conduct Regular Tabletop Exercises: Simulate various incident scenarios (e.g., ransomware attack, data exfiltration) in a discussion-based format. These exercises help your team understand their roles, identify gaps in the plan, and practice decision-making without real-world risk.
- Perform Realistic Drills (Simulations): Go beyond tabletop exercises with hands-on simulations that test your technical capabilities and response tools. This could involve mock phishing campaigns or simulated malware infections in a controlled environment.
- Validate Communication Chains: Regularly test your internal and external communication protocols to ensure rapid and accurate information dissemination during a crisis.
- Review and Update Annually (or More Often): The threat landscape evolves rapidly. Review your IRP at least once a year, or more frequently if there are significant changes to your IT infrastructure, business operations, or the cybersecurity threat environment.
- Incorporate Lessons Learned: After every real incident (no matter how small) or every exercise, conduct a thorough “post-mortem” analysis. Document what went well, what went wrong, and implement actionable improvements to your plan and processes.
- Stay Abreast of New Threats: Continuously educate your team on emerging threats, attack vectors, and industry best practices.
- Engage Third-Party Expertise: Consider involving external cybersecurity experts, like GiaSpace, to conduct independent assessments, penetration testing, or red team exercises that can uncover blind spots in your IRP.
How Does an Incident Response Plan Impact Business Continuity and Recovery?
The true value of a robust Incident Response Plan extends far beyond just mitigating a cyberattack; it is inextricably linked to your business’s ability to maintain continuity and achieve rapid recovery. An effective IRP serves as the critical bridge between a disruptive event and a swift return to normal operations.
- Minimized Downtime: By providing clear, pre-defined steps for containment and eradication, an IRP significantly reduces the time your critical systems are offline, directly impacting productivity and revenue.
- Data Integrity & Recovery: A solid plan includes strategies for secure data backups and efficient restoration, ensuring that even if data is compromised, it can be recovered accurately and quickly.
- Reputation Management: A well-executed response demonstrates competence and care to customers, partners, and stakeholders, protecting your brand’s reputation from long-term damage.
- Regulatory Compliance: Many industry regulations (e.g., HIPAA, PCI DSS, GDPR, state-specific data breach laws in Florida) mandate incident response capabilities. An IRP helps ensure you meet these obligations, avoiding hefty fines and legal repercussions.
- Financial Impact Reduction: As seen in industry reports, organizations with mature IRPs significantly reduce the financial costs associated with data breaches, from investigation to remediation and lost business.
- Enhanced Resilience: Ultimately, an IRP builds organizational resilience, transforming a potentially devastating incident into a manageable disruption, allowing your business to adapt and thrive even in the face of adversity.
What are the Common Challenges in Crafting an Incident Response Plan, and How to Overcome Them?
While developing an Incident Response Plan is vital, businesses often encounter hurdles. Recognizing these common challenges and knowing how to overcome them is key to building an effective strategy:
- Lack of Resources (Time, Budget, Staff): Many SMBs struggle with limited cybersecurity expertise or budget.
- Overcome: Start small with essential components, leverage free NIST resources, and consider partnering with an external IT service provider like GiaSpace for expert guidance and supplemental support.
- Insufficient Senior Leadership Buy-in: Without executive support, an IRP can lack the necessary authority and resources.
- Overcome: Emphasize the financial and reputational risks of not having a plan, using compelling statistics (like those in our stat table) to illustrate the business impact.
- Complexity & Overwhelm: The sheer scope of cybersecurity can be daunting.
- Overcome: Break down the plan into manageable phases (like the NIST framework), focus on your most critical assets first, and use templates or professional guidance.
- Outdated or Untested Plans: A plan that sits on a shelf is useless.
- Overcome: Schedule regular, mandatory training and tabletop exercises. Integrate IRP review into your annual IT strategy or compliance audits.
- Poor Communication: Siloed teams or unclear communication protocols can hinder response.
- Overcome: Establish clear communication trees and pre-approved messaging templates for various stakeholders (internal, external, media).
- Rapidly Evolving Threats: The cyber threat landscape is constantly changing, making it hard to keep a plan current.
- Overcome: Implement a continuous improvement loop. Subscribe to threat intelligence feeds and regularly update your plan based on new attack vectors and industry best practices.
What Tools and Technologies Support an Efficient Incident Response Process?
An effective Incident Response Plan is significantly bolstered by the right technological tools that enable faster detection, more efficient analysis, and streamlined communication. Here are key categories of tools that support an efficient IR process:
- Security Information and Event Management (SIEM): Aggregates and analyzes log data from various sources across your network to detect suspicious activities and potential incidents in real-time.
- Endpoint Detection and Response (EDR): Monitors individual devices (laptops, servers) for malicious activity, providing deep visibility and the ability to contain threats at the endpoint.
- Security Orchestration, Automation, and Response (SOAR): Automates routine security tasks and orchestrates complex incident response workflows, speeding up response times and reducing manual effort.
- Network Intrusion Detection/Prevention Systems (IDS/IPS): Monitors network traffic for signs of intrusion or malicious activity and can block detected threats.
- Firewalls & Next-Generation Firewalls (NGFW): Act as the first line of defense, controlling network traffic based on security policies.
- Data Loss Prevention (DLP): Prevents sensitive data from leaving your organization’s control, whether intentionally or accidentally.
- Threat Intelligence Platforms: Provide up-to-date information on emerging threats, vulnerabilities, and attack methodologies, enhancing proactive defense and identification.
- Backup and Disaster Recovery Solutions: Essential for recovering data and systems after an incident, minimizing downtime and data loss.
- Secure Communication Tools: Encrypted communication platforms ensure sensitive incident details are discussed securely.
Implementing and managing these tools effectively requires expertise. GiaSpace can help your Florida business select, deploy, and manage the right security technologies to support your incident response capabilities.
Key Metrics: How to Measure the Effectiveness of Your Incident Response Plan?
To truly understand if your Incident Response Plan is working, you need to measure its effectiveness. Tracking key metrics helps identify areas for improvement and demonstrates the value of your cybersecurity investments to leadership. Here are crucial metrics to monitor:
- Mean Time To Detect (MTTD): The average time it takes your team to identify a security incident from the moment it begins. A lower MTTD indicates better monitoring and detection capabilities.
- Mean Time To Contain (MTTC): The average time from detection to when the incident is successfully contained, preventing further spread. A lower MTTC signifies efficient containment strategies.
- Mean Time To Resolve/Recover (MTTR): The average time taken to fully resolve the incident and restore affected systems to normal operation. A lower MTTR demonstrates effective recovery processes.
- Number of Incidents: Track the total number of security incidents over time, categorized by type (e.g., malware, phishing attempts, data breaches).
- False Positive Rate: The percentage of security alerts that turn out to be benign. A high false positive rate can lead to alert fatigue and wasted resources.
- Cost Per Incident: Calculate the average financial impact of each incident, including direct costs (investigation, remediation) and indirect costs (lost productivity, reputational damage).
- IR Plan Compliance Rate: The percentage of incidents handled strictly according to the documented IRP.
- Training & Exercise Participation: Track the percentage of relevant staff participating in incident response training and drills.
- Customer/Stakeholder Impact: Measure the impact of incidents on customer service, brand reputation, and business operations.
Regularly analyzing these metrics allows GiaSpace to help your business refine its incident response strategy, making it more agile, efficient, and ultimately, more protective.
Outsourcing Cybersecurity Management? No Excuse!
Relying on an external team for cybersecurity? Excellent choice. But remember, it’s still crucial for internal stakeholders to understand their role in a crisis. Documentation of protocols, key contacts, and internal responsibilities can be a lifesaver.
Seeking Expert Assistance
Building an incident response plan internally can be effective, but sometimes external expertise can offer invaluable insights. Cybersecurity consultants can be a significant asset if you want a fresh perspective or a complete plan overhaul.
Conclusion: The Time to Act is Now
In the evolving digital landscape, threats are inevitable, but being ill-prepared isn’t. Prioritize the creation or refinement of your organization’s incident response plan. The safety and reputation of your organization depend on it.
Published: Aug 13, 2023







