In an era where cyber threats are becoming more sophisticated, protecting your business’s online presence requires more than just basic security measures. Threat intelligence services play a crucial role in monitoring and defending your domain from potential cyberattacks, unauthorized access, and fraudulent activities. By leveraging real-time data and proactive security measures, these services help ensure your domain remains secure and resilient against emerging threats.
In today’s interconnected world, cyber threats aren’t just evolving; they’re multiplying at an unprecedented rate. Traditional cybersecurity measures, while essential, often react to attacks after they’ve already begun. This is where Threat Intelligence Services step in.
Threat Intelligence (TI) is a sophisticated, data-driven approach that goes beyond basic security. It’s the process of collecting, analyzing, and refining information about potential and existing cyber threats, giving your organization a proactive edge. Think of it as having an elite team constantly monitoring the digital underworld, deciphering hacker chatter, analyzing malware patterns, and predicting the next wave of attacks before they hit your shores.
Why is this crucial for your business, especially in Florida? For small, medium, and large businesses alike, the stakes couldn’t be higher. A single data breach can cripple operations, devastate finances, and permanently damage your hard-earned reputation. From ransomware gangs targeting specific industries to phishing campaigns designed to steal sensitive customer data, the adversaries are relentless. Threat intelligence transforms your defense from a reactive scramble into a strategic, informed posture, allowing you to:
- Anticipate and Prevent: Identify emerging threats and vulnerabilities before they can be exploited.
- Prioritize Defenses: Understand which threats pose the greatest risk to your specific assets, allowing you to allocate resources effectively.
- Accelerate Response: If an incident occurs, contextual intelligence helps your team respond faster and more effectively, minimizing damage.
- Protect Your Brand: Safeguard your data, customer trust, and public image from the severe fallout of a cyberattack.
- Ensure Business Continuity: Minimize downtime and operational disruptions caused by unforeseen security incidents.
For businesses across Gainesville, Orlando, Jacksonville, Fort Lauderdale, and Miami, understanding the specific regional threat landscape is vital. GiaSpace’s threat intelligence services provide that localized insight, ensuring your defenses are aligned with the unique challenges faced by Florida enterprises.
How Threat Intelligence Services Work
1. Continuous Domain Monitoring
Threat intelligence services constantly scan the internet for any signs of suspicious activities related to your domain. This includes detecting unauthorized changes to your DNS records, monitoring domain registrations for potential phishing attempts, and identifying lookalike domains.
2. Real-Time Threat Detection
By leveraging artificial intelligence and machine learning, threat intelligence platforms analyze data in real time to detect potential cyber threats. They monitor global threat databases, dark web forums, and known malicious actors to identify risks before they escalate.
3. Early Warning Systems
Threat intelligence services provide alerts when suspicious domain activities are detected. These early warnings allow businesses to take immediate action, such as locking their domain, blocking malicious traffic, or adjusting security settings to prevent unauthorized access.
4. Incident Response and Mitigation
If a threat is detected, intelligence services provide actionable insights to help mitigate the risk. Security teams can use this information to investigate incidents, remove fraudulent domains, and strengthen domain security policies.
5. Brand Protection and Domain Reputation Management
Threat intelligence services help protect your brand by identifying and taking down fraudulent websites that attempt to impersonate your business. By securing your domain’s reputation, you reduce the risk of customer trust being compromised by malicious actors.
How Do Threat Intelligence Services Collect and Analyze Data?
The power of threat intelligence lies in its ability to transform vast amounts of raw, disparate data into clear, actionable insights. This isn’t just about scanning for known viruses; it’s a multi-faceted process that spans the digital globe.
GiaSpace’s approach to threat intelligence involves a continuous cycle of data collection, processing, and analysis, drawing from diverse sources:
- Open Source Intelligence (OSINT): We monitor publicly available information, including cybersecurity blogs, news articles, academic research, social media discussions, and even deep web forums where threat actors might discuss new tactics.
- Technical Intelligence: This involves gathering and analyzing technical indicators of compromise (IOCs) such as malicious IP addresses, domain names, file hashes, and specific malware signatures. Our systems constantly ingest data from network logs, endpoint telemetry, and global security feeds.
- Human Intelligence (HUMINT) & Expert Analysis: Our cybersecurity professionals stay abreast of the latest attacker techniques, tactics, and procedures (TTPs). We leverage industry partnerships, participate in intelligence-sharing communities, and apply expert human analysis to contextualize technical data and identify patterns that automated systems might miss.
- Dark Web Monitoring: Specialized tools and techniques are used to safely explore underground marketplaces, private forums, and illicit communities where stolen data is traded and attack plans are often discussed. This provides early warnings of potential data breaches or targeted campaigns.
- Vulnerability & Exploit Databases: We constantly cross-reference your systems and software against global vulnerability databases to identify known weaknesses that threat actors might exploit.
Once collected, this raw data undergoes rigorous processing, including normalization, de-duplication, and enrichment. Advanced analytics, often powered by AI (as we’ll discuss later), then identify patterns, trends, and anomalies. The goal is to separate the signal from the noise, providing our clients with precise, relevant, and timely intelligence that empowers them to make informed security decisions.
Key Components of a Comprehensive Threat Intelligence Program
A truly effective threat intelligence program is more than just a single tool; it’s a cohesive framework built on distinct but interconnected components. At GiaSpace, our comprehensive approach ensures your business receives layered protection and strategic foresight.
A robust threat intelligence program typically involves:
- Strategic Intelligence: This is the high-level view, providing insights into the overall cyber threat landscape, major threat actors (nation-states, organized crime, hacktivists), and their motivations. It helps leadership understand long-term risks and allocate resources for future security investments. For example, understanding a rise in ransomware targeting the healthcare sector would be strategic intelligence.
- Tactical Intelligence: This focuses on the specific TTPs (Tactics, Techniques, and Procedures) used by threat actors. It provides security teams with detailed information on how attacks are executed, enabling them to configure defenses, update security tools, and improve detection capabilities. This could include details on a new phishing technique or a specific malware delivery method.
- Operational Intelligence: This is about real-time, actionable data related to ongoing or imminent threats. It includes Indicators of Compromise (IOCs) like malicious IP addresses or malware hashes that can be immediately fed into firewalls, intrusion detection systems, and SIEM tools to block attacks in progress. It’s the “what to do right now” information.
- Vulnerability Intelligence: A dedicated focus on identifying and prioritizing software and system vulnerabilities. This component ensures that patches and configurations are applied strategically to close the most critical security gaps before they are exploited.
- Threat Hunting Capabilities: Going beyond automated alerts, threat hunting proactively searches your network for hidden threats, anomalies, or indicators of compromise that may have bypassed initial defenses. This relies heavily on operational and tactical intelligence to guide investigations.
- Reporting and Dissemination: Transforming complex intelligence into digestible, relevant reports for various stakeholders – from technical security teams to executive leadership – ensuring everyone understands the risks and the necessary actions.
GiaSpace integrates these components to provide a holistic threat intelligence solution that’s tailored to your unique business needs and the specific threat landscape of Florida.
Threat Intelligence vs. Traditional Cybersecurity: What’s the Difference?
It’s a common misconception that “cybersecurity” and “threat intelligence” are interchangeable. While closely related and interdependent, they serve distinct purposes within your overall defense strategy. Understanding the difference is key to building truly resilient protection.
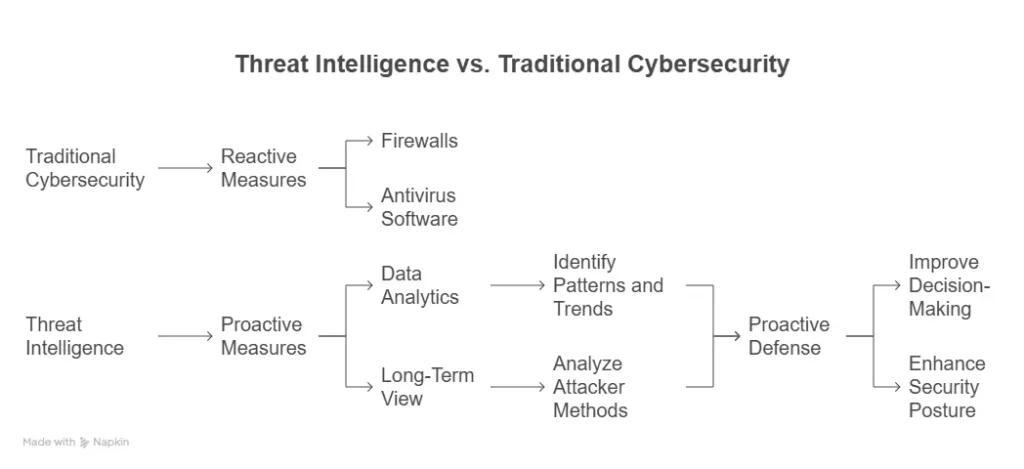
Here’s a breakdown:
| Feature | Traditional Cybersecurity (e.g., Firewalls, Antivirus) | Threat Intelligence Services |
|---|---|---|
| Primary Goal | React & Defend: Protect against known threats and vulnerabilities. | Predict & Proactively Prevent: Understand, anticipate, and mitigate emerging threats. |
| Approach | Reactive/Rule-Based: Blocks based on predefined signatures, rules, and known exploits. | Proactive/Contextual: Analyzes trends, actor motivations, and TTPs to predict future attacks. |
| Focus | Internal Systems: Securing your network, endpoints, and applications. | External Landscape: Monitoring the global threat environment and its relevance to you. |
| Information | Known malware signatures, blocked IPs, policy violations. | Emerging TTPs, hacker discussions, vulnerability exploit attempts, geopolitical influences. |
| Benefits | Foundational protection, compliance, basic incident response. | Reduced breach risk, faster incident response, informed strategic decision-making, competitive advantage. |
Think of it this way: Your traditional cybersecurity tools are your fortress walls, guards, and alarm systems – essential for defending against attacks at your perimeter. Threat intelligence, however, is your scout team and intelligence agency, gathering information from beyond your walls, identifying potential sieges, understanding the enemy’s strategies, and warning you long before they even reach your gates.
For businesses in Florida, this distinction is crucial. With the growing sophistication of cyber adversaries, relying solely on traditional defenses leaves you vulnerable to the unknown. GiaSpace combines robust traditional cybersecurity with cutting-edge threat intelligence to give you an unparalleled security posture.
Real-World Scenarios: How Threat Intelligence Prevents Specific Cyberattacks
It’s easy to discuss “proactive defense” in abstract terms, but how does threat intelligence truly prevent specific cyberattacks in the real world? Let’s look at some tangible examples where GiaSpace’s threat intelligence capabilities make a critical difference:
- Scenario 1: Preventing a Targeted Phishing Campaign.
- Without TI: Your employees might receive a highly sophisticated phishing email, carefully crafted to impersonate a known vendor. One click could lead to credential theft or malware infection, compromising your entire network.
- With TI: Our threat intelligence services detect discussions on dark web forums about a new phishing kit targeting businesses in the manufacturing sector (your industry). We identify the specific email patterns, sender domains, and malware payloads being used. This intelligence is immediately fed into your email filters and security awareness training, blocking the malicious emails before they ever reach your employees’ inboxes and educating them about the new threat.
- Scenario 2: Shutting Down Data Exfiltration Before It Happens.
- Without TI: An insider threat or a compromised account might slowly exfiltrate sensitive customer data to an unknown server, going undetected until it’s too late and the data appears on the dark web.
- With TI: GiaSpace’s continuous monitoring identifies a newly registered domain that perfectly mimics one of your trusted third-party vendors. Our intelligence indicates this domain is part of a command-and-control infrastructure for a known data exfiltration group. We proactively block communication with this domain at your firewall level, preventing any outbound data transfer from your network, even if an internal system were compromised.
- Scenario 3: Mitigating Zero-Day Exploits (Unknown Vulnerabilities).
- Without TI: A critical vulnerability in common software is discovered that has no patch yet (a “zero-day”). Attackers rapidly exploit this, compromising businesses globally before they even know they’re at risk.
- With TI: Our intelligence feeds pick up on early chatter about a zero-day exploit circulating in underground hacking communities, even before a public patch is available. While a permanent fix isn’t ready, we provide immediate tactical advice, such as temporary network segmentation, specific firewall rules, or intrusion detection signatures, to mitigate the risk until an official patch can be deployed.
These scenarios demonstrate that threat intelligence isn’t just about detecting; it’s about predicting, adapting, and defending against the unseen, keeping your business in Gainesville, Orlando, Jacksonville, Fort Lauderdale, or Miami one step ahead of the adversary.
The Role of AI and Automation in Modern Threat Intelligence
The sheer volume and velocity of cyber threats today make it impossible for human analysts to keep pace alone. This is where Artificial Intelligence (AI) and automation become indispensable allies in modern threat intelligence. At GiaSpace, we harness these advanced technologies to amplify our capabilities and deliver superior protection.
- Accelerated Data Ingestion and Normalization: AI-powered tools can rapidly collect, process, and normalize vast amounts of unstructured and structured data from countless sources – news feeds, dark web forums, technical reports, and internal logs. This automates the tedious work of data preparation, allowing human analysts to focus on higher-level tasks.
- Pattern Recognition and Anomaly Detection: Machine Learning (ML) algorithms are adept at identifying subtle patterns, anomalies, and correlations in massive datasets that would be invisible to the human eye. This helps in detecting novel threats, identifying suspicious behaviors, and even predicting future attack vectors.
- Threat Prioritization and Scoring: AI models can assess the relevance and criticality of identified threats to your specific environment. By correlating external intelligence with your internal network telemetry, AI helps prioritize alerts, reducing “alert fatigue” for security teams and ensuring focus on the most impactful risks.
- Automated Response and Remediation: In some cases, AI and automation can trigger immediate, predefined responses to detected threats, such as isolating a compromised endpoint, blocking a malicious IP address, or disabling a suspicious user account. This dramatically reduces Mean Time to Respond (MTTR), limiting the damage from an attack.
- Natural Language Processing (NLP) for Unstructured Data: NLP allows AI systems to understand and extract critical information from human language sources like hacker forums or social media, even when the language is informal or coded. This provides deeper insights into attacker motivations and methods.
While AI and automation are powerful, they are not a replacement for human expertise. Instead, they serve as force multipliers, empowering GiaSpace’s cybersecurity professionals to operate with greater speed, accuracy, and foresight, ensuring comprehensive threat intelligence for your Florida business.
Best Practices for Domain Security with Threat Intelligence
To maximize the effectiveness of threat intelligence services, businesses should:
-
Enable Multi-Factor Authentication (MFA) – Strengthen domain security by requiring additional verification steps for access.
-
Regularly Review DNS Settings – Ensure that all DNS records are correctly configured and monitor them for unauthorized changes.
-
Use Domain Locking Features – Prevent unauthorized domain transfers by enabling registrar locks.
-
Implement SSL Certificates – Secure website connections to protect user data from interception.
-
Conduct Routine Security Audits – Regularly evaluate security measures to identify potential vulnerabilities.
Measuring the ROI of Threat Intelligence: Tangible Benefits for Your Business
Investing in threat intelligence isn’t just a cost; it’s a strategic investment that delivers a significant return on investment (ROI) by protecting your most valuable assets. While some benefits are easily quantifiable, others contribute to the long-term resilience and reputation of your business.
Here’s how to view the tangible ROI of GiaSpace’s Threat Intelligence Services:
- Reduced Breach Costs: As noted in the IBM Cost of a Data Breach Report 2023, organizations with strong threat intelligence capabilities experience significantly lower breach costs. By proactively identifying and mitigating threats, you avoid the massive expenses associated with data recovery, regulatory fines, legal fees, notification costs, and reputational damage.
- Minimized Downtime & Business Disruption: A successful cyberattack can halt operations, leading to lost productivity and revenue. Threat intelligence minimizes this risk by preventing attacks before they can cause downtime, ensuring business continuity and maximum operational efficiency.
- Faster Incident Response (MTTD/MTTR Reduction): When an incident does occur, threat intelligence provides immediate context about the attacker’s TTPs and the nature of the threat. This drastically reduces your Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), limiting the attack’s impact and speeding up recovery.
- Optimized Security Spending: With clear insights into the most relevant threats, you can allocate your cybersecurity budget more effectively, investing in the right defenses and avoiding unnecessary expenditures on less critical risks. This targeted approach maximizes the impact of every security dollar.
- Enhanced Reputation & Customer Trust: Preventing breaches and demonstrating a proactive security posture builds unwavering trust with your customers and partners. This intangible benefit translates into sustained business growth and a stronger market position, especially vital in competitive Florida markets.
- Improved Compliance Posture: Proactive threat intelligence strengthens your ability to meet regulatory requirements and industry standards, reducing the risk of non-compliance penalties and demonstrating due diligence to auditors.
By preventing costly attacks, streamlining security operations, and safeguarding your reputation, GiaSpace’s Threat Intelligence Services deliver a clear and measurable return, making it an indispensable part of your business’s growth and resilience strategy in Florida.
Choosing the Right Threat Intelligence Provider for Your Business in Florida
Selecting a threat intelligence provider is a critical decision that impacts your entire cybersecurity posture. For businesses operating in Florida, understanding regional specificities and finding a partner with local expertise can make all the difference.
When evaluating potential partners for your threat intelligence needs, consider these key factors:
- Relevance and Customization: Does the provider offer intelligence tailored to your industry, geographic location (like Florida), and specific threat landscape? Generic feeds can lead to “alert fatigue” and missed critical threats.
- Breadth and Depth of Sources: Do they draw from a wide array of sources, including OSINT, dark web, technical, and human intelligence? The more diverse the inputs, the more comprehensive the outputs.
- Actionable Insights: Is the intelligence truly actionable, providing clear recommendations for mitigation and defense, rather than just raw data? Can it be integrated seamlessly into your existing security tools?
- Expertise and Support: Do they have a team of seasoned cybersecurity analysts who can interpret complex intelligence and provide expert guidance? What kind of ongoing support is offered?
- Integration Capabilities: Can their threat intelligence feeds and platforms integrate with your current security infrastructure (SIEM, EDR, firewalls) to automate defenses and streamline operations?
- Proactive vs. Reactive: Does their service emphasize proactive threat identification and prevention, or is it primarily reactive? A truly effective provider will help you anticipate threats.
- Reputation and Trust: Look for a provider with a proven track record of protecting businesses and a strong reputation within the cybersecurity community.
GiaSpace stands as a premier choice for businesses across Gainesville, Orlando, Jacksonville, Fort Lauderdale, and Miami. With over 20 years of experience, we combine global threat intelligence capabilities with a deep understanding of the unique challenges faced by Florida enterprises, ensuring you receive fast, friendly, first-time fix IT support that includes cutting-edge threat intelligence. We don’t just provide data; we provide peace of mind.
Frequently Asked Questions About Threat Intelligence Services
To further clarify how Threat Intelligence empowers your business, here are answers to some common questions:
Q1: Is Threat Intelligence only for large enterprises?
Absolutely not. While large enterprises may have dedicated security teams, small and medium businesses (SMBs) are often equally, if not more, vulnerable to cyberattacks due to fewer resources. Threat intelligence scales to provide critical protection for businesses of all sizes, offering crucial insights that SMBs might otherwise lack.
Q2: How quickly can GiaSpace’s Threat Intelligence detect emerging threats?
Our systems are designed for near real-time ingestion and analysis. While the time to detect a new emerging threat can vary, our continuous monitoring and AI-powered analysis aim to identify and alert you to potential risks as quickly as they appear in the global threat landscape, often before they become widespread.
Q3: Can Threat Intelligence integrate with my existing security tools?
Yes, a key benefit of modern threat intelligence is its ability to integrate with your current security infrastructure, including Security Information and Event Management (SIEM) systems, Endpoint Detection and Response (EDR) solutions, firewalls, and more. This enhances the effectiveness of your existing tools by feeding them timely, actionable threat data.
Q4: What kind of reports will I receive from GiaSpace’s Threat Intelligence?
GiaSpace provides tailored reports that translate complex threat data into clear, actionable insights for both technical teams and executive leadership. These can include daily threat briefings, weekly summaries of emerging threats, incident-specific intelligence reports, and strategic overviews of the changing cyber landscape relevant to your industry and location in Florida.
Q5: How does Threat Intelligence help with regulatory compliance?
Many industry regulations and data protection laws (e.g., HIPAA, PCI DSS) require robust security measures and incident response capabilities. Threat intelligence helps you meet these requirements by providing the foresight to prevent breaches, strengthening your incident response planning, and demonstrating a proactive approach to cybersecurity, which can be crucial during audits.
Published: Jan 12, 2025







